LexisNexis® BehavioSec®
Actionable Intelligence from Human Interactions
BehavioSec®, an industry pioneer and technology leader, is now LexisNexis® Risk Solutions.
Speak with our team of experts to discover how behavioral biometrics can
support your organization to solve even the most complex identity trust
and fraud challenges.
The Smart Tech That Gets Smarter With Every Movement, Building Identity Trust and Lowering Risk
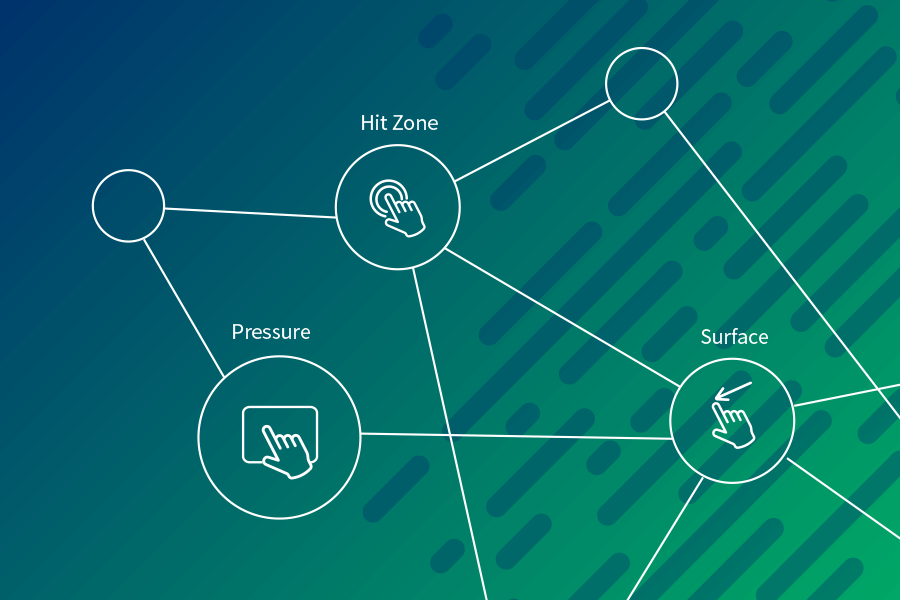
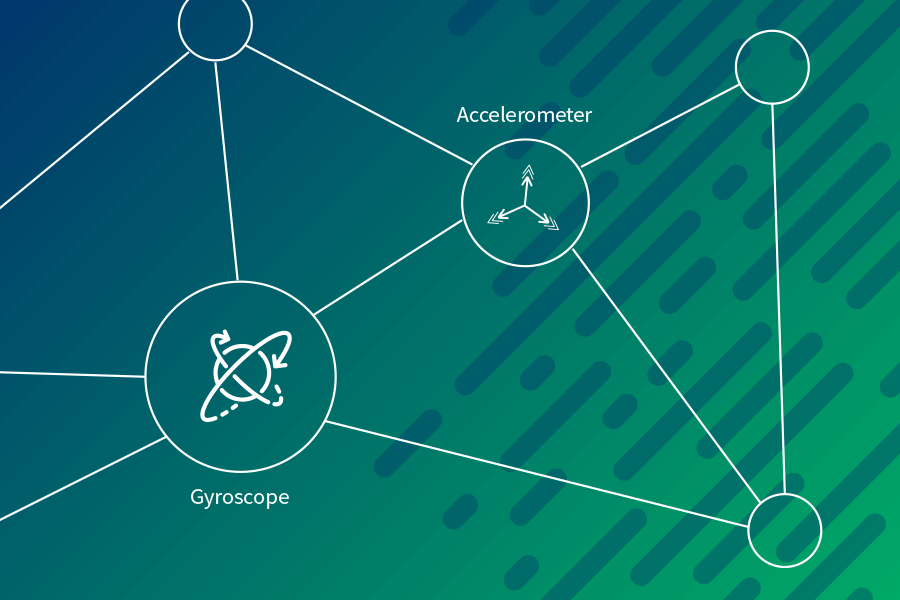
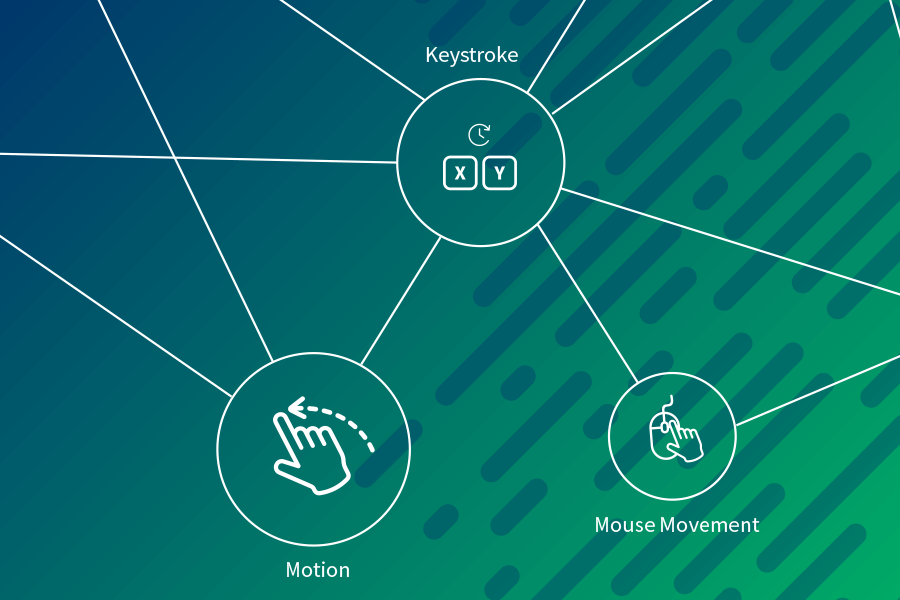
Our solution analyzes each session for environmental risk factors, using a rich set of intelligence signals that yields a near real-time authenticity score.
Working passively behind a digital interaction, our solution helps you ensure that your genuine customers and users enjoy powerful online experiences without friction, while simultaneously placing you in a strong position to respond as needed to real risks and behavioral anomalies.
What is Behavioral Biometrics?
Learn more about how LexisNexis BehavioSec streamlines the user and
customer experience while combating fraud
Improve Experience Throughout Digital Journeys
Combine data from billions of global transactions with LexisNexis Behaviosec
for actionable insights at every stage of interaction.
New Account Creation and Onboarding

Account Login

Account Management
Transaction Fraud and authorized transfer scams
How Can LexisNexis BehavioSec Support Your Organization's Challenges?
LexisNexis BehavioSec streamlines the customer experience while combating fraud.
Why LexisNexis BehavioSec?
Trusted by leading institutions around the world to enhance fraud prevention and authentication
without impacting customer experience, revenue streams or workflow efficiency.
Recognize Genuine Customers and Users
Improve Efficiency
Intercept Coaching and Scams
Detect Non-Human Behaviors
Reduce Friction for Genuine Customers and Users
Reduce Complexity
LexisNexis BehavioSec is now available alongside LexisNexis ThreatMetrix.
Fortify trust in customers and users, and their transactions, with a robust combination of
behavioral biometrics and digital identity intelligence.
Related Products
-
Digital Identity Network
Gain the ability to recognize good, returning customers and weed out fraudsters, all in near real time
Learn More -
FraudPoint®
Combat identity fraud with sophisticated scoring and leading analytics
Learn More -
LexisNexis® Emailage®
Get a clear picture of who is behind a transaction and the associated risk, so your team can automate decision workflows, improve customer experience, all in near-real time
Learn More -
ThreatMetrix®
Enable cybersecurity and risk management through data science innovation and shared intelligence
Learn More